Each time the signature is applied Signify connects with the Managed HSM and uses the key to sign. The Managed HSM is certified according to the US Federal Information Processing Standard (FIPS) - 140 L2.

Certification and Compatibility
Signify adheres to security best practices in its development. Our digital signature engine is built upon the Digital Europe eSignature DSS library, ensuring full compliance with the PAdES standard mandated by the eIDAS regulation.
Additionally, Signify holds ISO/IEC 27001 certification, underscoring our dedication to information security. Our system undergoes regular penetration testing by a third-party company accredited with the CREST standard.
Your data is securely stored in the AWS Stockholm data center, which also aligns with the ISO/IEC 27001 and ISO/IEC 27018 security standards. The data is consistently maintained in an encrypted state.





Signing Key Protection
Security of a signing solution depends on how adequately the signing keys are protected. Signify uses Managed HSM (Hardware Security Module) to securely store cryptographic keys. Our signature keys are generated inside the Managed HSM and never leave it.

Data Protection and access control
Documents are encrypted both on transport and application layers and stored only in already encrypted state in the AWS Stockholm data center. This ensures that only the document owner and authorized users have access to the document contents.
All user interactions with Signify are conducted over a secure TLS 1.2 or TLS 1.3 connection, therefor, all information is encrypted between the web-browser and Signify server.
Document contents or decryption keys are not under the control of the database administrator or the system administrator. The decryption keys are not accessible to any Signify support operators or any other users.
When the document is shared for review and signature, the document does not leave Signify, instead users are notified via email or SMS. They use link that was shared to them to access and view the document using the Signify secure document viewer.
The document owner can define the access rights for any recipient, including:
- Who can view the document and in which order;
- Authentication methods for each user (e.g. one-time SMS code);
- Permissions to download document, download evidence report and other;
- The time interval during which the recipient can view the document via shared link.

Cryptography
Signify uses the most secure algorithms and protocols recognized and used by various international government and banking institutions. In addition, in each document signed on a platform Signify embeds a digitally-signed timestamp from a Time Stamp Authority - Globalsign TSA.
On the Signify platform, we use the most secure algorithms and protocols, including:
- For signature we use 2048-bit RSA key, which is industry best practice. For signature hashing SHA-384 algorithm is used. For data encryption AES/GCM with AESWrap algorithm is used with 256-bit key length.
- Signify performs validation of the full chain of signer's certificate, according to the rules of IETF PKIX RFC5280.
- The system does the verification of the status of the digital certificate and the corresponding keys at the moment of signing. The CRL/OCSP response is embedded in the signature itself to ensure its long-term validation.
- Signify uses Time Stamp Authority - GlobalSign TSA, that allows us to prove the fact of the signature based on third party, each signature has embedded GlobalSign timestamp in it.



AATL signatures - source of trust
We use digital certificates from CAs which are registered as part of the Adobe AATL program. In our case - GlobalSign CA.
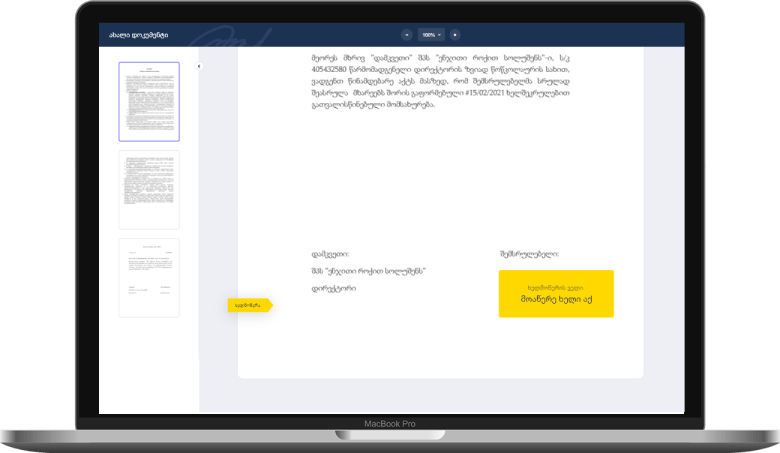
When verifying digitally signed PDF documents outside the signing service it is very useful that end-users can trust the digital signatures immediately and avoid seeing messages within their Acrobat Reader that the signature is valid but the signer's identity is not trusted. To avoid this issue the signing solution needs to support digital certificates from CAs which are registered as part of the Adobe AATL program. This ensures that when opening documents signed on Signify with Acrobat Reader, you will see the following message:

Long-term validation
Like signing a paper document, in the case of an digitally signed document, it must be verifiable at a later date. This is an area we have invested in heavily by following the latest advanced, long-term digital signature and preservation standards.
When signing paper documents you implicitly trust the fact that the signature will be verifiable for several years into the future. Similarly in the electronic world, digitally signed documents must be verifiable at a later date. For example, in many jurisdictions and regulated industries, business documents need their authenticity to be verifiable for at least 7 to 10 years or more. Not all signing solutions are capable of offering a long-term validation capability due to several reasons:
- Cryptography is a dynamic field, where different algorithms are discarded as insecure as the time passes.
- The digital certificates which are used to apply signatures are time-limited with an average validity of 1-3 years.
- The PDF content can render unreadable after a certain time, if not approached properly.
This is an area we have invested in heavily by following the latest advanced, long-term digital signature and preservation standards as explained below.
PAdES (PDF Advanced Electronic Signature) - Part 4 - Long Term Archivable
PAdES is a set of restrictions and rules for PDF and ISO32000-1 standards that make the document compatible for electronic signatures. It is published by ETSI (European Telecommunications Standards Institute) as TS 102 778. Specifically, PAdES Part 4 complies with the Georgian and European qualified electronic signature standard. In the signed document it becomes possible to add additional trusted Timestamp integration (embed), not only when signing directly, but also after it. This makes it possible to extend the validity of a signed document despite the obsolescence of the cryptographic algorithms used at the time of signing.
PDF/A
PDF / A is an ISO-standardized version of PDF designed for archiving and long-term storage. PDF / A differs from standard PDF in that it prohibits various functionalities that may be problematic for long-term archiving (eg font linking or encryption). This makes it possible to archive the document and read it in the long run.

Secure document viewer
A Secure Document Viewer is essential for users to clearly review what they are about to sign. Within the industry this is called WYSIWYS (What You See Is What You Sign) and ensures the user is signing the document that is presented on the screen.
It must not be possible for malicious code to show one thing to the user and get them to sign something else behind the scenes. Signify uses a secure document viewer that always shows a flattened image of the document. The user always sees exactly what they are about to sign.
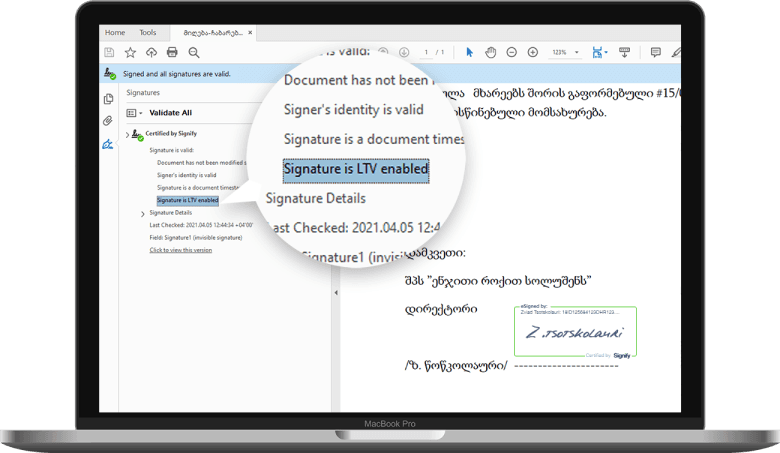
In addition to this, when signing documents on Signify each version of the document is preserved before every subsequent signature in the PDF document itself. With this feature, anyone can see what the document looked like before a particular signature was applied. This is a standard feature available within our signed PDF documents. You can see this snapshot versions in Acrobat Reader by right-clicking a signature field and then selecting the “view signed version”.